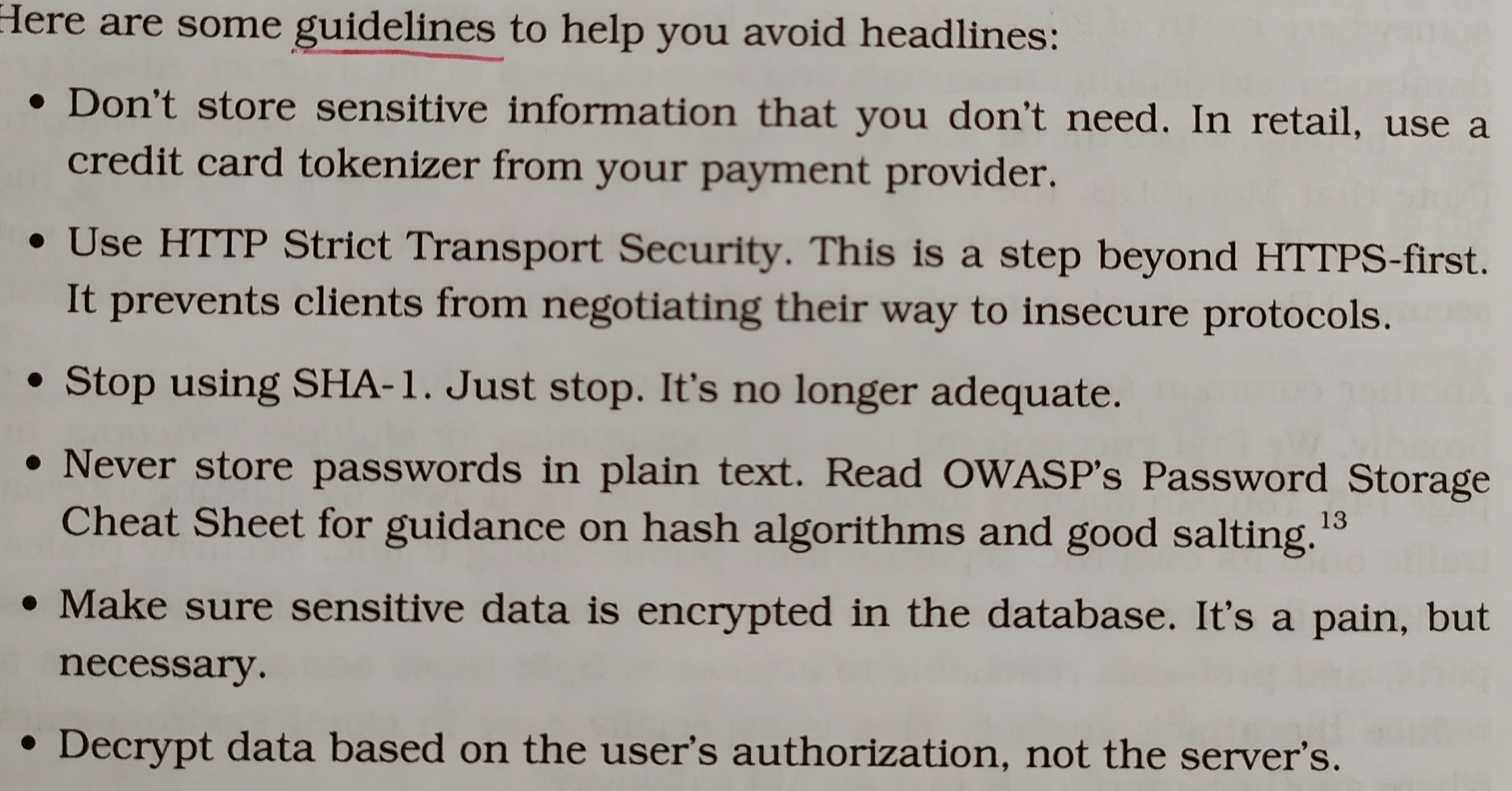
Sensitive Data Exposure
All the valuable things people can steal from you or use against you.
eg. credit cards, medical records, insurance files, purchasing data, emails
pattern: applications request data encryption keys, which are encrypted themselves anti-pattern: don’t leave decryption keys laying around where and attacker could retrieve them (eg. in memory) AWS Cloud: use AWS Key Management Service (KMS) On Premise: HashiCorp Vault anti-pattern: half-heartedly using an encryption tool you picked
(src: